

Great input and you’re absolutely correct. Very important to safeguard backups.
2023 Reddit Refugee
On Decentralization:
“We no longer have choice. We no longer have voice. And what is left when you have no choice and no voice? Exit.” - Andreas Antonopoulos


Great input and you’re absolutely correct. Very important to safeguard backups.


Use of a VPN depends on your privacy threat model.
Using VPN at all times while using the internet like one normally does is beneficial only to the extent that you encrypt your traffic and prevent your ISP from spying on you… mostly. But if you’re logging into known accounts associated with you, then it’s a moot point. Your traffic is encrypted, but your use of services leaves an easy to follow cookie trail of where you’ve been.
If your privacy threat model is much more serious, then you wouldn’t login to any known accounts while on your VPN. You wouldn’t use services that can be pinpointed to you.
Hence, use a VPN to your discretion. If you generally don’t want your ISP spying on you, keeping it on is always best practice. If you have more things to hide, you’d want to use Tor while on VPN and of course don’t use any services that could be linked to you.


Nothing much you can do except make it harder for nefarious parties to get your information. If you’re in the U.S. most of your information is public. With two pieces of info about you, you’re one Google search away from your name, physical address, schools you went to, where you’re employed, etc. You can’t stop this, so just make it harder when your data does get leaked.
Here are my best practices:


It’s been a day. We pine for our hero. Will you answer the call?


100% agree. I grew up on Super NES and owned every console gen from Nintendo up through Switch. Got into PC gaming 7 years ago, and then picked up a PS5 on a ridiculous deal to try to enter into their market and play some games. Astro Bot is a charming and incredibly fun video game. So much love was poured into this game.
It’s an incredible game and it deserves all of the awards it earned. I still love all the main Mario games I’ve played, and Mario Odyssey was a wonderful and charming game, too. Astro Bot is certainly not a “we already have Mario at home” game - I hold it up there with one of my favorite platformers I’ve ever played.
It’d be great if it could get ported to PC, but they would have to significantly adjust the game controls to get around the purposefully tight integration with the PS5 controller. Playing that game with the PS5 controller was so much fun.
Edit: fixed some mobile typos


I decided to stop playing Mario and Luigi Superstar Saga because the game became too tedious and I wasn’t having as much fun with it. A shame because I loved M&L Dream Team and wanted to start from its roots.
Now currently playing Sea of Stars and Hades.


Indeed. I’ve been radicalised by Ubisoft.
In 2012 I bought Splinter Cell Blacklist for Wii U. Loved it so much I paid for all the DLC, just like I did with Assassin’s Creed III also on Wii U. Not too long ago, Ubisoft announced they were terminating legacy activation servers, and multiplayer modes would no longer function. But this also meant that without those activation servers, I would lose access to the DLC I paid for (as Ubisoft disclosed) because the game phones their activation servers and authenticates if I own the DLC. With enough public gamer outrage and pushback, Ubisoft walked back this decision… for now.
I thought I was safe buying physical games like I always have. I thought I was safe if the DLC was downloaded to the console. If this legacy server decommissioning went through, I would never be able to legally play the stuff I paid for and should own. Lesson learned, and every last ounce of ever wanting to play a modern Ubisoft game died in about ~2020 when they announced this. I don’t trust them, and I’m glad to see their company is beginning to tank because they stopped innovating and making good games like they used to decades ago.
When I wanted to replay Blacklist recently, I pirated it. The pirated copy ran better than the copy I own on Steam and Uplay - no crashes every 30 minutes (seriously, look it up), no bugs, etc. I didn’t want to play the Wii U copy because it’s a very slow console and the loading times for levels is insane (10+ minutes to load in due to the archaic Wii U architecture, back when I first played it in 2012).
I’m receiving a better service from the pirates rather than Ubisoft. Not that I want to play any modern Ubisoft games, but this whole “ownership” thing has made me question every digital purchase I’ve made. Now, I rip all my Blu Rays to PC and archive them. I buy on GOG, and only buy on Steam if I can’t get it on GOG.
Sorry for long story, Ubisoft just really pisses me off and they destroyed the last thread of good will I had for them. I’ll just stick to playing Beyond Good and Evil on my GameCube if I get nostalgic for the games they made that had heart and innovation.


For my PC I prefer headphones for the immersion. When on the Steam Deck, I use in ear buds. I have a handful of Apple ear pods I’ve amassed over the years that I’ll use when I’m trying to get some quick gaming in. If I get a chance to really sit down and game for an hour or more, I use my JBL Quantum TWS with the USB C receiver. Total immersion, excellent sound quality, noise canceling, and incredible latency. Battery life could always be better, but they’ll comfortably get me through a solid gaming session on the Deck.
I don’t use the speakers on my Deck at all. I probably should play some games with it and see how I like it.


Get the original on GOG without DRM or forced PSN.


Barges into room.
Them: “Are you hacking, son?
Me: “No.”
Them: “Cool. I’m just a hotel employee, and I only have understanding of computers at an end-user level. Plus, I see you’re not wearing a hoodie and sunglasses while being hunched over a laptop. Have a nice day and enjoy your stay at the Hilton!”


Exactly, and this is additionally why it is predatory: you can’t opt out.
It’s similar to Facebook. If you never in your life ever created a profile, well, Facebook has one for you regardless.
The only way you can opt out of bluetooth beacons is to not bring your phone/smart watch/etc, or have either a hardware switch that disables your network functions or put it in a faraday cage. Also, because of data profiles and associations, if you’re walking into a store with your partner, expect that your partner should do the same or else it’s all moot. You’re associated with your partner and thus tracking and profiling occurs anyway.


No tinfoil hat needed. Retail stores are equipped with bluetooth beacons that tracks and monitors customer behavior. This in turn can be sold for targeted advertising. Another scary thought is that the tracking is so precise, it measures the distance your phone is from a product, including height. How high is the phone from the ground? The data points can be extrapolated to influence product placement: what products and prices influenced a customer to bend down and look at/interact with the product? How long were they in close proximity with the product? Based on the phone’s orientation, were they bent down to look at or passing by the product (indicating that they stopped for a separate reason and not necessarily for the product)? Did they buy it? Were they looking for coupons in my “retail store app” while next to the product, or somewhere else in the store? Where do customers often stop or gather in order to browse through coupons? Could we place Y products there? Where should we put the product in stores to maximize sales? What ads can we send to them as they arrive at the store? Based on aggregated data with the rich profile we built for this customer, are they likely to sign up for our rewards credit card? What is this customer’s income level? Have they purchased X product recently? What part of town do they live in? What products are popular there? Et cetera ad nauseum.
Tracking is so predatory. Makes me look at my smart phone with disgust as the years go by, and I periodically grapple with the decision if a smart phone is even right for me or if it’s time to stick to a computer and a truly dumb phone going forward.
Some public info about Bluetooth beacons: https://www.nytimes.com/interactive/2019/06/14/opinion/bluetooth-wireless-tracking-privacy.html
Want to find Bluetooth beacons? Simply install a Bluetooth scanner app from your phone and head to a store to see them.
Here’s how Shopify engages businesses on how to utilize Bluetooth beacons with their software package. Bought anything online? That site was most likely powered by Shopify: https://www.shopify.com/retail/the-ultimate-guide-to-using-beacon-technology-for-retail-stores


There’s the official Jellyfin app for Apple TV. It works very well with only minor UI bugs when browsing libraries. Nothing that detracts from or reduces the quality of the service.


deleted by creator


You can customize how the extension handles cookie banners. See an example of current settings on most updated extension at time of this comment:
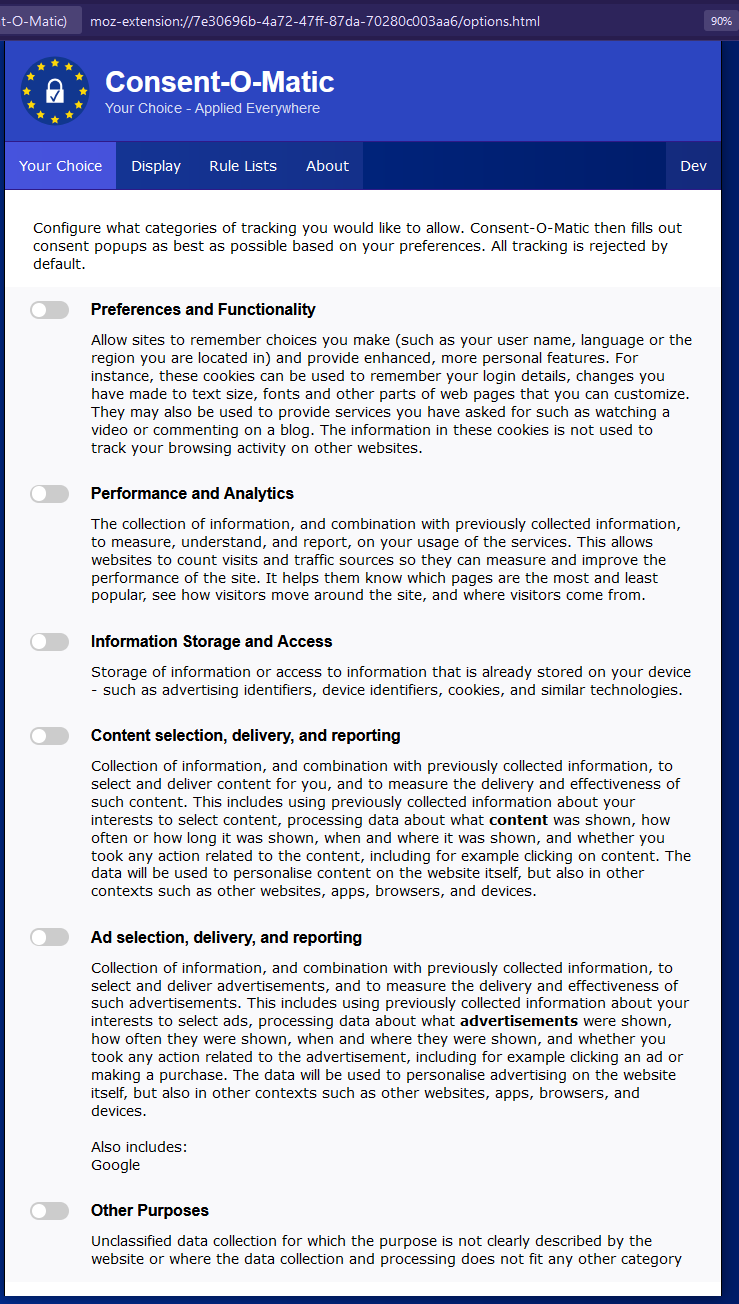


@BMP5k@feddit.uk , can you help here? Thanks


Oof! I definitely can raise an Enhancement request in their GitHub to see if they can take on adding that functionality.
If anyone can get me the exact link of whatever OP experienced, I can log it there.


Get yourself the Consent-o-Matic browser extension and watch these “we and our 8000 partners (hungrily) value your privacy” banners disappear.
If you stumble upon a web site that Consent-o-Matic does not handle, you can simply click the extension, click “Submit for Review”, and the devs will shortly add support for that site.
HTTPS with no VPN:
You trust the web site to encrypt your data if and only if the web site has properly implemented encryption along with encrypted DNS traffic. Sometimes you make a connection to HTTP before you’re redirected to HTTPS. Your ISP can see what web sites you visit, but the ISP can’t see what you’re doing because the traffic is encrypted so long as encryption is implemented correctly. ISP knows you went to https://www.website.com/.
Conclusion: Your ISP knows exactly what web sites you visit, but can’t see what you’re doing on the web site (if encryption is properly configured by the web site provider).
HTTP or HTTPS with trusted VPN (e.g., Mullvad):
You trust the VPN provider. Your connections are encrypted entirely. Your ISP can’t see what web sites you’re visiting nor can they interpret your traffic.
Conclusion: Your ISP is completely blind to what you’re doing and where you’re going.
ExpressVPN:
PureVPN:
Here are more sources I won’t quote, but you can read: