Thank you for letting me know what software not to use; good bot
- 0 Posts
- 190 Comments
I use ansible on one of my side projects; I use puppet at work. It’s the same reason I use raw docker and not rancher+rke2… it’s not about learning the abstractions; it’s about learning the fundamentals. If I wanted a simple abstraction I’d have deployed truenas and Linuxsserver containers instead of Taco Bell programming everything myself.
Sure. I have an r630 that is configured as an NFS server and a docker host called vacuum. There is a script called install_vacuum.sh that with a single command, can build the server to my spec from a base install of Ubuntu 24.04. it has functions to install base packages from repositories, add new repositories, set up users, create config files for NFS, smb, fstab, crontab, etc… once an NFS server exists on my network, any other server could be my docker host. My docker host is set up from a script install_containers.sh. as with before, it does all the things to get me a basic docker host, firewalled, and configured for persistence via my NFS server. It also has functions to create and start docker containers for all of my workflows (Plex, webserver, CA, etc), and if those containers don’t exist, it will build a docker image for said workflow based on a standardized format (you guessed it) bash build script for the containers. There is automation via cron on whatever host runs docker to build and update the containers once a week, bare-metal servers update themselves nightly, rebooting when necessary via unattended-upgrades.
Basically, you break everything down into the simplest function possible, have everything defined via variables in shared configurations that everything sources before running, and you have higher and higher level functions call other functions until you have a single function that cascades into a functioning system. Does that make sense?
Not sure if many people do what I do, but instead of taking notes I make commented functions in bash. My philosophy is: If I can’t automate it; I don’t understand it. After a while you build enough automation to build your workstations, your servers, all of your vms and containers, your workflows, etc, and can automate duplicating / redeploying them whenever required. One tarball and like 6 commands and I can build my entire home + homelab.

 0·8 months ago
0·8 months ago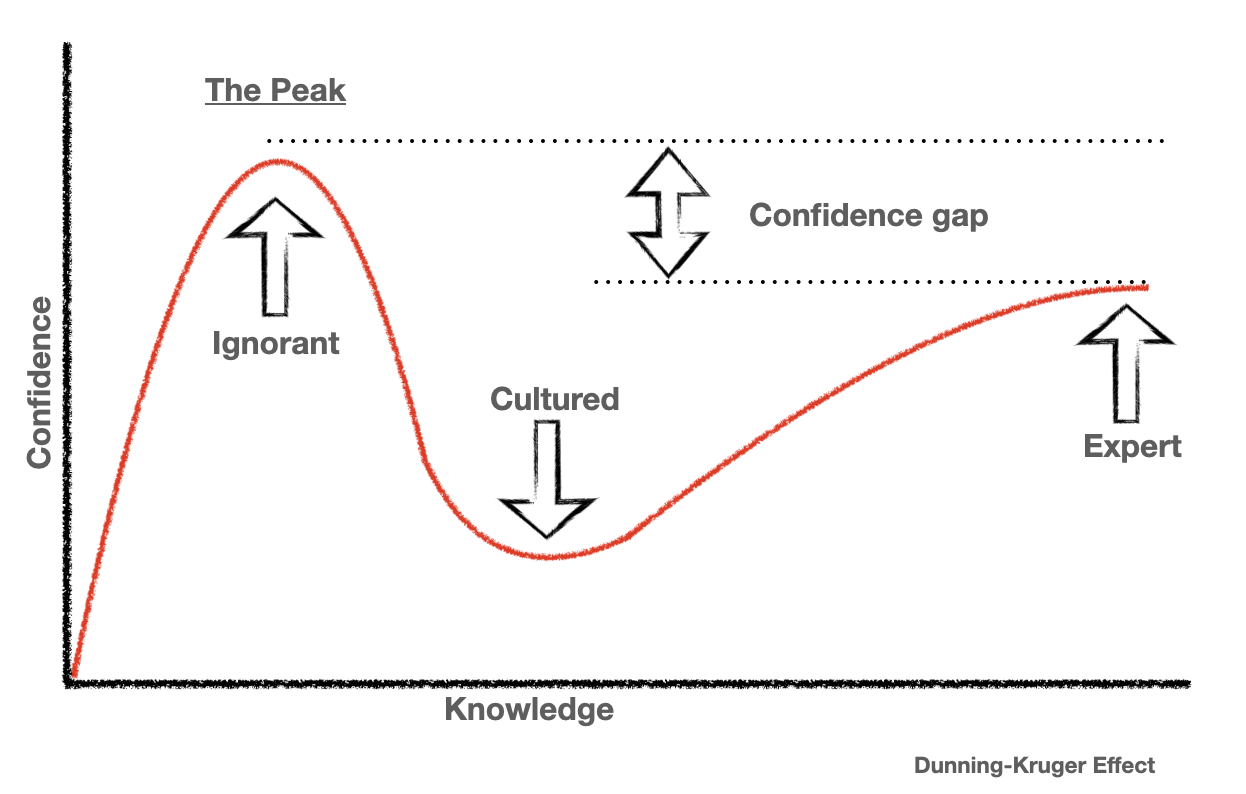
The thing about rational actors, is when given the same information they should make the same choices. I would argue that they’re most likely, instead, just at the peak of mt. stupid

 0·8 months ago
0·8 months agoWe shouldn’t blame the victims that society failed to properly educate. You’re right that if people intimately understood apple the way you probably do, they’d never buy an apple product. I would argue, however, that it’s a failing of education not an informed choice to be corporately cucked.

 0·8 months ago
0·8 months agoI don’t think anyone should expect a battery replacement to be free after 10 years, but it shouldn’t cost $100,000

 0·8 months ago
0·8 months agoJust because you can’t use it doesn’t mean a hacker can’t. If someone discovered a vulnerability in the 3g handshake or encryption protocol, it could be an avenue for an RCE.
I run ubuntu’s server base headless install with a self-curated minimal set of gui packages on top of that (X11, awesome, pulse, thunar) but there’s no reason you couldn’t install kde with wayland. Building the system yourself gets you really far in the anti-bloatware dept, and the breadth of wiki/google/gpt based around Debian/Ubuntu means you can figure just about any issues out. I do this on a ~$200 eBay random old Dell + a 3050 6gb (slot power only).
For lighter gaming I’ll use the Ubuntu PC directly, but for anything heavier I have a win11 PC in the basement that has no other task than to pipe steam over sunshine/moonlight
It is the best of both worlds.

 3·9 months ago
3·9 months agothe best way to learn is by doing!

 2·9 months ago
2·9 months agoI just built my own automation around their official documentation; it’s fantastic.
https://www.wireguard.com/#conceptual-overview

 2·9 months ago
2·9 months agovyatta and vyatta-based (edgerouter, etc) I would say are good enough for the average consumer. If we’re deep enough in the weeds to be arguing the pros and cons of wireguard raw vs talescale; I think we’re certainly passed accepting a budget consumer router as acceptably meeting these and other needs.
Also you don’t need port forwarding and ddns for internal routing. My phone and laptop both have automation in place for switching wireguard profiles based on network SSID. At home, all traffic is routed locally; outside of my network everything goes through ddns/port forwarding.
If you’re really paranoid about it, you could always skip the port-forward route, and set up a wireguard-based mesh yourself using an external vps as a relay. That way you don’t have to open anything directly, and internal traffic still routes when you don’t have an internet connection at home. It’s basically what talescale is, except in this case you control the keys and have better insight into who is using them, and you reverse the authentication paradigm from external to internal.

 304·9 months ago
304·9 months agoTalescale proper gives you an external dependency (and a lot of security risk), but the underlying technology (wireguard) does not have the same limitation. You should just deploy wireguard yourself; it’s not as scary as it sounds.

 0·9 months ago
0·9 months agoWhat if he wasn’t speeding, and didn’t dismiss dangerous civil behavior as something he should be allowed to pay 0.0001% of his net worth for and move on without consequence?
We should be one of those countries where civil infraction penalties are calculated based on net worth.

 91·9 months ago
91·9 months agoFail2ban and containers can be tricky, because under the hood, you’ll often have container policies automatically inserting themselves above host policies in iptables. The docker documentation has a good write-up on how to solve it for their implementation
https://docs.docker.com/engine/network/packet-filtering-firewalls/
For your usecase specifically: If you’re using VMs only, you could run it within any VM that is exposing traffic, but for containers you’ll have to run fail2ban on the host itself. I’m not sure how LXC handles this, but I assume it’s probably similar to docker.
The simplest solution would be to just put something between your hypervisor and the Internet physically (a raspberry-pi-based firewall, etc)

 0·9 months ago
0·9 months agoDevil’s Advocate:
How do we know that our brains don’t work the same way?
Why would it matter that we learn differently than a program learns?
Suppose someone has a photographic memory, should it be illegal for them to consume copyrighted works?
It’s fuckin’ art though

 0·9 months ago
0·9 months agoI believe it was a musk move that changed the default sort order from “latest first” to “most engaged” as an intentional inconvenience to encourage users to make accounts and log in.


I am also curious