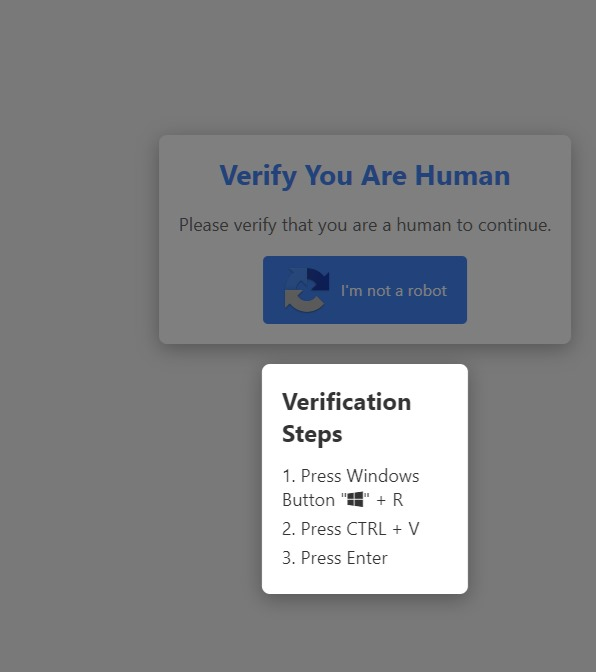
Anybody got more info on the actual payload?
powershell.exe -eC [payload_w_base64]is mentioned here.-eCjust means encoded command afaik.Deep analysis here https://denwp.com/anatomy-of-a-lumma-stealer
Thanks for sharing.
I also added that website to my RSS reader.
Seen this on the powershell subreddit before, it just downloads and runs another executable.
That is extremely hilarious
Except for the fact that a lot of less tech savvy people will fall for it.
Instructions were unclear, ransomware dev now owes me 0.15 bitcoin.
ah, think this is like one of those survey scams.
Thats why on Linux you need to run the sudo command and type the root password (or user password) to install something. I get this isn’t Linux but its a serious security vulnerability that someone could run a super user level command by clicking yes on a confirmation box that pops up so often that nobody thinks twice.
The goal is not always to “take control” of the whole system. A cryptolocker that makes all your files unreadable will happily run in user space.
Also, you’re forgetting that windows also have UAC, and that people will happily type the admin password of their device when asked to, because they’ve been conditioned to not care by badly made stuff. And, while win+r is unlikely to work in most Linux DE I know about, triggering a visual prompt that ask for your password is also a thing.
There is not much difference between common Linux distro and windows as far as seizing user files with malware is concerned, aside from the fact that no website will care to try telling you “press alt+space” instead of “win+r”.
The behavior is configurable just like it is on linux, UAC can be set to require a password every time.
But I think its not set this way by default because many users don’t remember their passwords, lol. You think I’m kidding, you should meet my family…
Also, scripts can do plenty without elevation, on linux or Windows.
It should be default, its a good security practice and not every app needs super user permissions.
You don’t need root access to steal all of the data that your user account has access to.
If Linux was more popular, you would definitely see a Linux variant of this doing the exact same thing.
The only issue I see with targeting Linux is the sheer variety of Desktop setups. Finding one keyboard shortcut and payload that will work on even just the majority of distros would be a challenge.
(Citation needed)
But something like this can still erase everything stored in your home folder or launch further exploits to gain root or something.
Its a lot harder and can do significantly less damage if it doesnt have root privileges, its like how putting a lock on the door to your house wont stop thieves but its better then not having one.
Bruh, let’s say an attacker deleted all of my important documents, say book drafts, and assume I don’t have a backup.
Now my progress has been set back six months and the publisher is angry.
Would I care if they deleted my system files or not?
Or, session cookies. They don’t need special privilege to access, and if you grab all of someone’s cookies, you can probably get some valid session cookies for logged in accounts just by checking for some common domains in one/by keyword.
From there, it would be trivial to get into email, social media, and other accounts to do other things with.
This reminds of when I was 13 I used to tell my opponents in Warcraft 3 that pessing alt+q+q quickly reveals the map. It’s a shortcut for closing the game. Worked way to many times
I do see this working
Don’t have to tell me, I just tried summoning quillbeasts while looking at health bars
We’d constantly get people by telling them holding alt and typing fax would get mirc to give them ops. Usually about a quarter of the channel would drop out.
btw if you want to try and hack me, my IP is 127.0.0.1
also makes the victims self selecting, much like the deliberate spelling errors in scam mails.
ALT+F4 for free funds, opened alot of slots on bfh servers whenever my friends couldn’t join.
was funny when someone said “alt f4” and 3 people immediately leave LOL
Haha, god I loved doing this on Counter-Strike. “Did you guys hear about the hidden tit pics in counter strike? No shit, hold alt and press f4 and it shows the best tits I’ve ever seen. I don’t know how game developers get away with this stuff.”
Half the lobby is gone, the other half is laughing.
/disco mode on
Yeah, and you can dupe items in RuneScape by dropping them and pressing Alt+F4. Don’t worry, I’ll stand way over here to prove I’m not trying to steal it. If I try to pick up the item you’ll see me move, and you can just pick it up first.
The day of a new patch in WoW I said in general chat “wow, they finally put a confirmation when you type /gquit , crazy how long it took” and sit in town and watch peoples guild names disappear
It seemed odd to me that a Web site could write to or read from the clipboard without the user approving it. That would be a pretty obvious security and privacy issue. From what I gather, on Chrome sites can write to the clipboard without approval, but they need approval to read. On Firefox and others any access requires permission. Thus this exploit seems limited to Chrome users.
It seemed odd to me that a Web site could write to or read from the clipboard without the user approving it
Yeah, that’s a security hole rhat I hadn’t been aware of.
not when there was a user intent like clicking a button.
For example in this screenshot, it’s likely that there’s only the “verify I’m human” button first, you click it, the steps pop up, and at the same time the command ist copied into your clipboard
Why isn’t the default behavior for browsers to not allow access to the clipboard? Similar to how it prompts you for access to camera/microphone
Edit: On a per-site basis, like if you use the Zoom website it asks you for access to the webcam, would something like this work for clipboard as well or would it break stuff?
The browser can’t access your clipboard contents without permission, but it can place text into the clipboard.
The problem is people the talking the copied text and pasting it into the command prompt.
but it can place text into the clipboard.
Only as the result of a user interaction, for example by pressing a button.
From the Browser’s viewpoint, would there be any difference if the webpage has a JS button to put something in the clipboard, or it having code running in the background that puts things into the clipboard at page load?
It’s not like there’s that much of a difference, as far as the Browser is concerned.
would there be any difference if the webpage has a JS button to put something in the clipboard, or it having code running in the background that puts things into the clipboard at page load?
Clicking a button shows user intent, whereas a page load doesn’t. No user expects loading a page to overwrite their clipboard, but every user that clicks a “Copy to Clipboard” button does expect it.
Yeah that’s what I’m curious about; I’m used to copying code snippets or codes from websites by clicking a button (presumably through some browser API?), but am just now realizing that this in itself has security implications.
Using noscript or some such JS blocker would prevent this but break a lot of other things in the process. That’s why I’m wondering why the API isn’t locked down via some user prompt.
In Firefox, you can disable the clipboard events. I’ve done this for the rare case of me copy+pasting a password and forgetting to clear the clipboard after.
On Android, I’ve noticed that it’s possible for apps to read from the clipboard, to read OTP tokens for example. Since I noticed that a while back, I’ve always been wary of the clipboard on any device I’ve used.
There is no inherent security problem with changing the content of the clipboard. That doesn’t do anything until the user pastes it somewhere; of course if that “somewhere” is a command prompt, then that is a security problem, but users really ought to check what they’re pasting there before they execute it (yeah, I know, “ought to”).
It would be possible to do it the way you say, but that would mean that the user would need to allow that for many websites; I don’t think copying from apps like Google Docs would work anymore, and “here’s your access token, click here to copy it to the clipboard” features certainly wouldn’t.
The screenshot in the OP would then probably be changed to include a step “click: allow clipboard access”; I think most people who fall for the screenshot in the OP would also fall for that.
Exactly. Furthermore they’d probably just include it in those instructions “Step 1: when the box pops up with clipboard press allow”
Exactly, copy requires a click but there’s no rule that the copy has to look like anything particular
It doesn’t necessarily need a click - it can be triggered by a keypress too (eg at my workplace we have a few internal pages where you can press a keyboard shortcut to copy a shortened URL for the current page).
It has to be something the browser considers a user interaction, meaning the user has expressed an intent to perform the action. That’s usually a button press or keypress.
This is actually pretty smart because it switches the context of the action. Most intermediate users avoid clicking random executables by instinct but this is different enough that it doesn’t immediately trigger that association and response.
That’s going to catch some people, especially older ones.
Yet if I was helping my elders over the phone, I’d get all sorts of “What Windows key?”, “I can’t find that Control key”, or “I did that key, the plus key, and then my hand slipped and I minimized everything.”
Failed to execute child process: “calc.exe” (No such file or directory)… hehe

/s no I wouldn’t actually implement it
Yeah, right? Captchas have trained users to do whatever weird thing a webpage tells them to do, so now people will do this without thinking about it.
Yeah I sent the screenshot to my parents right away, I think they would know better but better be safe than sorry.
Kinda brilliant to disguise malware as a captcha, though. I won’t be surprised.
Usually I warn my 81 year old dad about these scams. Don’t think I need to worry about this one, he wouldn’t be tech savvy enough to find the windows button
When I saw a women get hacked aftermath. They installed remote access software, however in her downloads you could see the 10 duplicates.
The scum fuck scammer on the phone had to spend at least 45 minutes trying to get them to navigate to their downloads and run the installer.
Our elders are safe from this one lol
Sometimes I feel bad for scammers because I know how long it takes just to freaking reset a password on legitimate support calls at work (and usually that’s someone who’s put in a vague ticket saying “software isn’t working” so I emailed them a “I’m not a psychic” email with a link to schedule a call which requires one to schedule on the next business day just to finally talk on the phone and identify what they couldn’t write out in their ticket 2 days ago) but then I remember that they’re fucking scammers and often fully aware of what they’re doing
Same here, nothing to worry about
I cant believe they made captcha that only works on windows
You (probably) wouldn’t see this page unless you were on Windows
diabolical